Empowering Your Business Through Unwavering Cybersecurity


Expert Penetration Testing
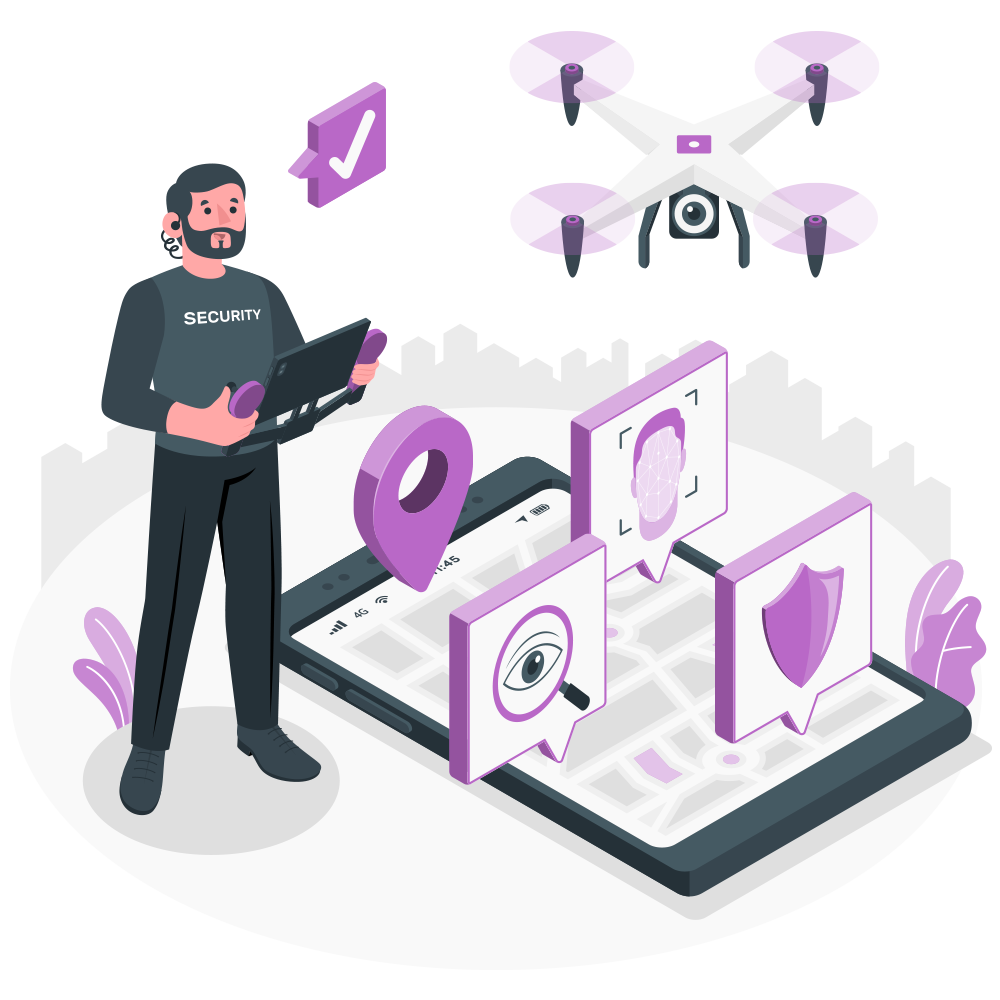
Comprehensive Application Security
Our holistic application security model ensures robust protection across every layer of your software, from initial architecture design down to meticulous code implementation. Beepeeo works diligently to ensure that no vulnerability goes unnoticed or unpatched, building a secure foundation for your critical applications and safeguarding your valuable data throughout their entire lifecycle.
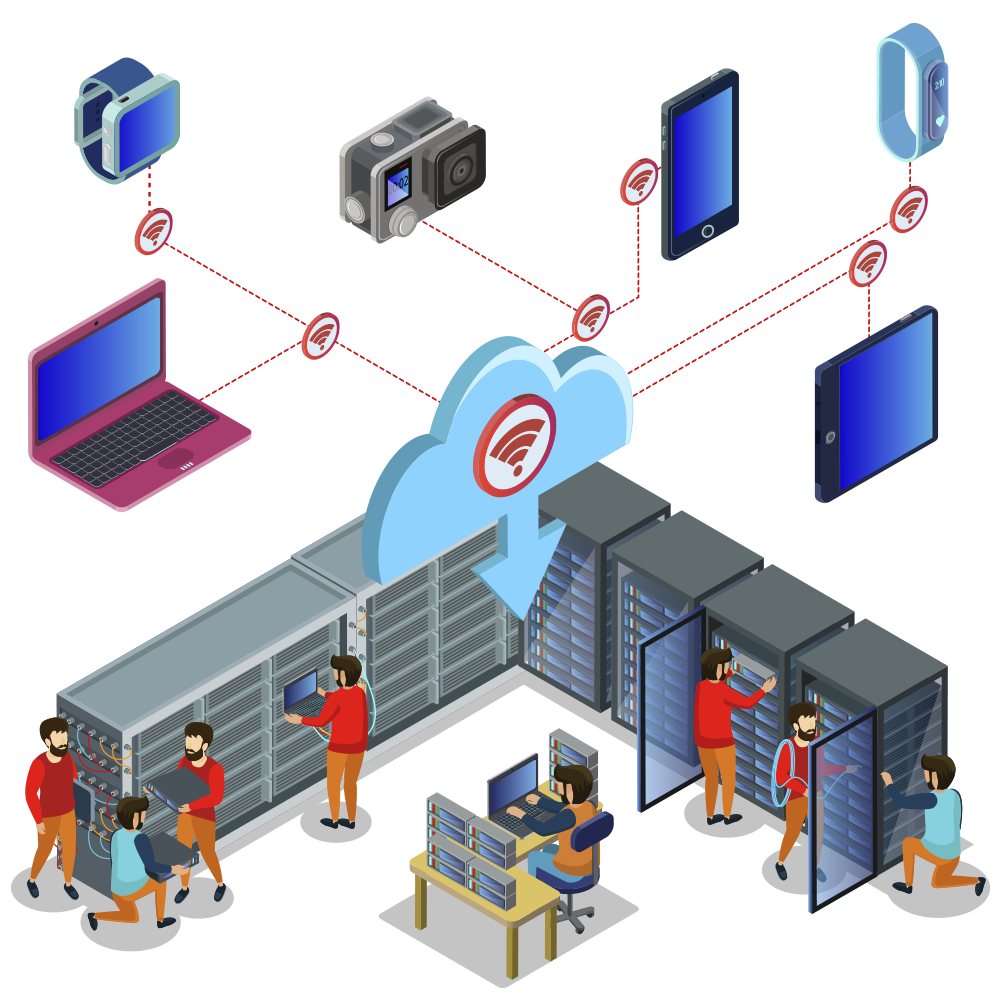
Robust Network Infrastructure Security
Strategic Red-Teaming Engagements
Our custom AI solutions are built specifically for your unique business challenges, offering tools that automate processes and improve decision-making. From enhancing customer engagement to optimizing internal workflows, our AI applications are designed to bring tangible business benefits. Tailored to fit your industry, these solutions help you gain a competitive edge.

Proactive Security Consulting & Strategy
Unlock the power of your data with our comprehensive data analysis services that provide actionable insights for informed decision-making. By leveraging real-time analytics, your business can adapt quickly to market changes and identify new growth opportunities. Our solutions turn complex data into clear, digestible reports that empower your team to take action

Rapid Incident Response & Remediation
Advanced
Cybersecurity and Information Security Services at Beepeeo Ltd.
-
What is the primary benefit of investing in cybersecurity for my business?
-
Cutting-Edge Methodologies & Tools
-
Proactive Threat Intelligence
-
Regulatory Compliance & Risk Management
Customized Security Frameworks
We believe that effective security solutions are never one-size-fits-all. Beepeeo develops bespoke security frameworks, policies, and procedures that are precisely aligned with your industry, compliance obligations, and specific risk appetite. Our tailored approach ensures optimal data protection without impeding your operational agility.Cutting-Edge Methodologies & Tools
Our team continuously adopts and masters the latest cybersecurity methodologies, threat intelligence, and state-of-the-art tools. This commitment to innovation allows us to employ the most effective techniques for threat detection, vulnerability assessment, and defense, providing you with a superior level of cyber protection.Proactive Threat Intelligence
Staying ahead of cybercriminals requires a proactive stance. Beepeeo continuously monitors the global threat landscape, gathering and analyzing real-time threat intelligence. This allows us to anticipate emerging attacks and fortify your defenses before they are exploited, shifting from a reactive to a predictive security model.Regulatory Compliance & Risk Management
Navigating the complex web of cybersecurity regulations (e.g., GDPR, HIPAA, PCI DSS) can be challenging. Beepeeo helps your organization achieve and maintain compliance, implementing robust controls and processes that mitigate regulatory risks and demonstrate due diligence to auditors and stakeholders.Strategic Insights to Enhance Business Value Through Cybersecurity and Information Security Services

Cybersecurity as a Business Enabler
Beyond just protection, cybersecurity at Beepeeo is viewed as a strategic enabler for business growth and digital transformation. By embedding security by design into your operations, we help you innovate securely, expand into new markets confidently, and leverage emerging technologies without compromising your integrity or reputation.

Building Unwavering Trust and Market Credibility
A strong cybersecurity posture directly translates into enhanced trust with your customers, partners, and investors. By demonstrating a proactive commitment to protecting sensitive data and maintaining operational resilience, Beepeeo helps you build a reputation for reliability, providing a distinct competitive advantage in the marketplace.

Ensuring Business Continuity and Resilience
Cyber threats can lead to significant operational disruptions and financial losses. Beepeeo's comprehensive information security services focus on building true organizational resilience, minimizing downtime, and ensuring rapid recovery from any cyber incident. This strategic foresight protects your bottom line and guarantees the continuity of your essential business functions.
FAQs
How secure are IoT devices?
How often should my company conduct penetration testing?
What's the difference between vulnerability scanning and penetration testing?
How can Beepeeo help my business comply with data protection regulations?
What steps should my company take immediately after a cyber incident?
Is cybersecurity only a concern for large enterprises?
How does cybersecurity contribute to my company's reputation?
What is Red Teaming, and how does it differ from traditional penetration testing?

Our team builds and maintains custom web applications designed to expand your business reach.
Develop high-performance mobile apps with us, designed for both iOS and Android platforms.
We manage and deliver projects focused on developing responsive, SEO-friendly user interfaces, ensuring optimal performance across all devices and platforms.

We conduct thorough testing to ensure your software works flawlessly from the start.
We design tailored databases that ensure data security and boost your decision-making capabilities.
Our designs are visually appealing, functional, and aligned with your business goals.d needs.

Quickly and reliably deliver software with our expert DevOps practices, enhancing workflow efficiency.
We develop robust backend systems that power high-performance AI/ML and IoT applications, ensuring seamless data processing, real-time analytics, and scalable integration.
Create customized online stores with us, optimized for user satisfaction and business growth.


